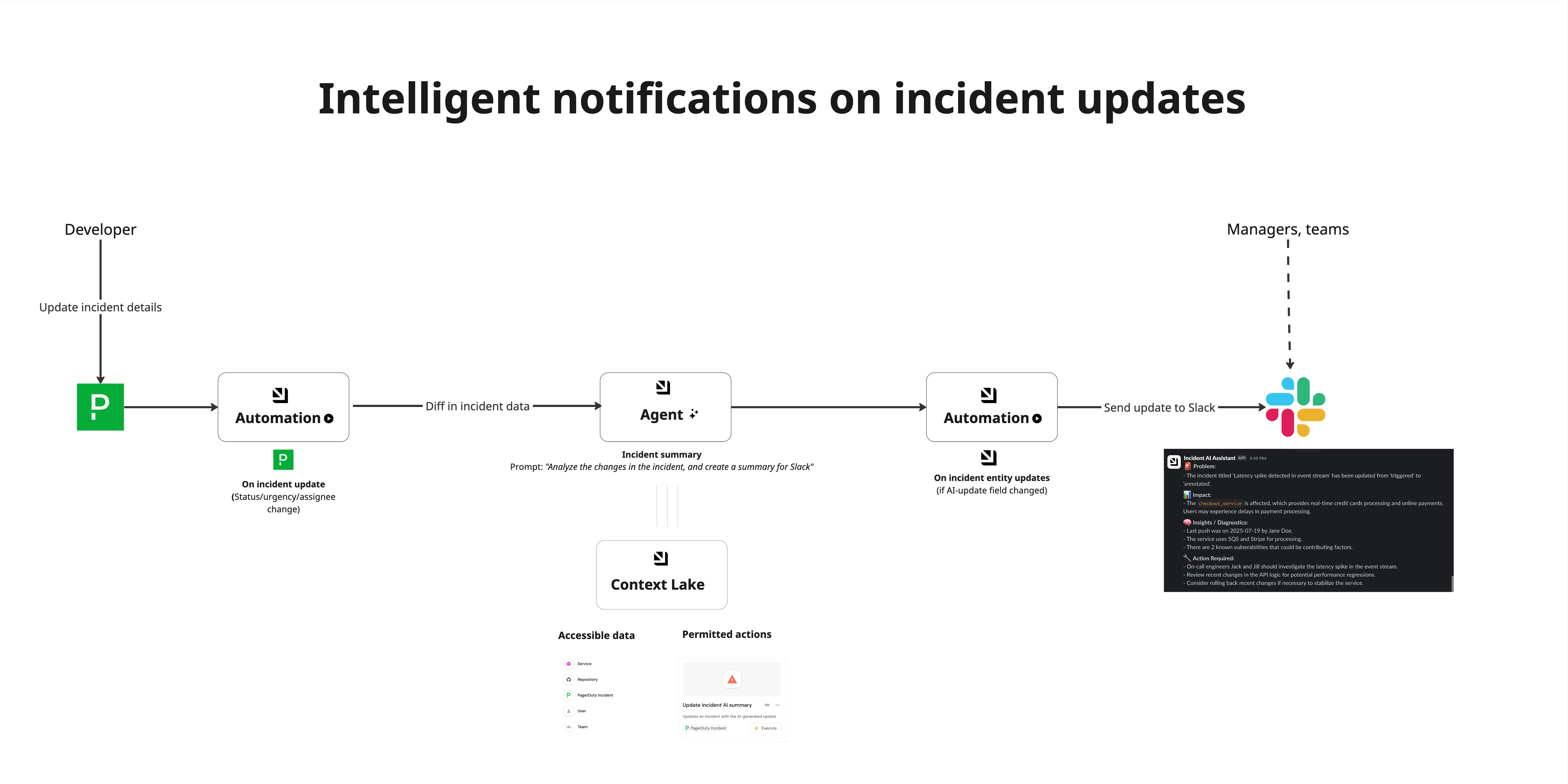
Generate incident updates with AI
When you are busy fixing an incident, you do not have time to write updates. Yes, others still need to know what is going on. In this guide, we will learn how to build an AI agent that generates incident updates and sends Slack notifications with relevant technical context.
Common use cases
- Automatically generate contextual incident updates when incidents are updated.
- Send notifications to Slack with relevant technical context.
- Provide on-call engineers with enriched incident information.
Prerequisites
This guide assumes the following:
- You have a Port account and have completed the onboarding process.
- PagerDuty integration is installed in your account.
- GitHub integration is installed in your account.
- You have access to create and configure AI agents in Port.
While this guide uses PagerDuty and GitHub, you can adapt it for other incident management tools like OpsGenie or FireHydrant, and other Git providers like GitLab or Azure DevOps.
Set up data model
We will create and configure blueprints to support our AI-enhanced incident management workflow. This includes setting up the incident data model and enriching it with repository metadata.
Update the incident and service blueprints
To enable AI-generated incident updates and Slack notifications, update your blueprints as follows:
-
Add an
ai_updateproperty to the incident blueprint-
Go to the builder page of your portal.
-
Find and select your incident blueprint (e.g.,
pagerdutyIncident). -
Click on
{...} Edit JSON. -
Add the following property to the
propertiessection:AI update property (click to expand)
"ai_update": {
"type": "string",
"title": "AI Update"
} -
Click
Saveto update the blueprint.
-
-
Add a
slack_channelproperty to the service blueprint-
Go to the builder page of your portal.
-
Find and select your service blueprint (e.g.,
pagerdutyService). -
Click on
{...} Edit JSON. -
Add the following property to the
propertiessection:Slack channel property (Click to expand)
"slack_channel": {
"type": "string",
"title": "Slack Channel"
} -
Click
Saveto update the blueprint.Slack channel configurationThis step is optional. You can choose to:
- Send notifications to a static channel (hardcoded in the automation).
- Store the Slack channel in other hierarchies (e.g., on the incident itself).
- Use different channels based on incident severity or team.
-
Update repository blueprint with additional context
When installing the GitHub app, the Repository blueprint is created by default. However, we need to add additional properties to enrich incident updates with repository metadata.
-
Go to the builder page of your portal.
-
Find and select your existing repository blueprint (e.g.,
githubRepository). -
Click on
{...} Edit JSON. -
Add the following properties to the
propertiessection:Additional repository properties (click to expand)
"last_contributor": {
"title": "Last contributor",
"icon": "TwoUsers",
"type": "string",
"format": "user"
},
"last_push": {
"icon": "GitPullRequest",
"title": "Last push",
"description": "Last commit to the main branch",
"type": "string",
"format": "date-time"
},
"vulnerabilities": {
"type": "number",
"title": "Known Vulnerabilities",
"description": "Number of critical security vulnerabilities"
} -
Click
Saveto update the blueprint.
Add repository relation and mirror properties
We will now enhance the incident blueprint with mirror properties from the repository blueprint to provide better context for AI-generated incident updates.
-
Go to the builder page of your portal.
-
Find the
pagerdutyIncidentblueprint and click on it. -
Add a relation to the
Repositoryblueprint. -
Add the following mirror properties:
Mirror properties configuration (Click to expand)
{
"mirrorProperties": {
"repository_last_push": {
"title": "Repository Last Push",
"path": "repository.last_push"
},
"repository_last_contributor": {
"title": "Repository Last Contributor",
"path": "repository.last_contributor"
},
"repository_vulnerabilities": {
"title": "Repository Vulnerabilities",
"path": "repository.vulnerabilities"
},
"repository_readme": {
"title": "Repository README",
"path": "repository.readme"
},
"slack_channel": {
"title": "Slack Channel",
"path": "pagerdutyService.slack_channel"
}
}
} -
Click
Saveto apply the mirror properties.
Set up self-service action
We will create a self-service action that the AI agent can run automatically to update the incident with the AI update. This approach provides more flexibility and allows manual triggering.
-
Go to the self-service page of your portal.
-
Click on
+ New Action. -
Click on the
{...} Edit JSONbutton. -
Copy and paste the following JSON configuration:
Update incident with AI update action (Click to expand)
{
"identifier": "update_incident_with_ai_update",
"title": "Update Incident with AI Update",
"icon": "Alert",
"description": "Updates an incident with the AI-generated update",
"trigger": {
"type": "self-service",
"operation": "DAY-2",
"userInputs": {
"properties": {
"ai_update": {
"title": "AI Update",
"type": "string",
"format": "markdown"
}
},
"required": [
"ai_update"
],
"order": [
"ai_update"
]
},
"blueprintIdentifier": "pagerdutyIncident"
},
"invocationMethod": {
"type": "WEBHOOK",
"url": "https://api.getport.io/v1/blueprints/pagerdutyIncident/entities/{{ .entity.identifier }}",
"agent": false,
"synchronized": true,
"method": "PATCH",
"headers": {
"RUN_ID": "{{ .run.id }}",
"Content-Type": "application/json"
},
"body": {
"properties": {
"ai_update": "{{ .inputs.ai_update }}"
}
}
},
"requiredApproval": false
} -
Click
Saveto create the action.
Create AI agent
Next, we will create an AI agent that generates helpful incident updates with contextual information.
Configure the incident update AI agent
-
Go to the AI Agents page of your portal.
-
Click on
+ AI Agent. -
Toggle
Json modeon. -
Copy and paste the following JSON schema:
Incident update AI agent configuration (Click to expand)
{
"identifier": "incident_update_ai",
"title": "Incident Update AI",
"icon": "Alert",
"team": [],
"properties": {
"description": "AI agent that generates helpful incident updates and sends them to Slack with on-call tagging",
"status": "active",
"prompt": "You are an expert incident management AI agent generating clear, contextual summaries for Slack notifications.\nYour task is to produce Slack-compatible summaries for incident updates shared with engineering and on-call teams. Focus on clarity, relevance, and next steps.\n\nYour Slack summary MUST follow this structure and tone:\n\n- 🚨 *Problem:* Brief summary of what changed and why it triggered this update.\n- 📊 *Impact:* Which services or what is affected? Any delivery, uptime, or user-facing issues?\n- 🧠 *Insights / Diagnostics:* Add key technical context from repository metadata: last commit, contributor, vulnerabilities, etc or draw from your technical knowledge on what would have caused this.\n- 🔧 *Action Required:* List next steps for the on-call team. Be specific about what they need to check or resolve.\n\n🔧 **Slack Output Rules**\n* NEVER USE `**bold**` or `[text](url)` — instead use:\n * `*bold*` for emphasis\n * `<https://url.com|Label>` for links\n* Use emoji to indicate sections: `🚨`, `📋`, `👥`, `🔄`\n* Use bullet points (`-`) for clarity\n* Separate sections with one line space (not headers)\n* Never include raw markdown headers like `###` or `---`\n* Your final output **must** look clean when copy-pasted into a Slack message.\n\n*After generating your update, you MUST ALWAYS run the 'update_incident_with_ai_update' action to save the update to the incident record.*\n\n## Sample Response Format\n🚨 *Incident Update: API Latency Spike on analytics-service*\n\n*Problem:*\n`analytics-service` has breached its latency SLO for the past 15 minutes. Response time spiked from 800ms to 4.5s\n\n*Impact:*\nThis service powers real-time analytics for customer dashboards. Users may experience slow or failing dashboard loads, particularly in high-traffic regions.\n\n*Insights/Diagnostics:*\n- The latest deployment (2025-07-21 13:03 UTC) introduced new filtering logic\n- Recent commits by Maria include changes to Redis query batching and fallback caching\n- Maria is not currently on-call. Assigned engineers: Omri and Tal.\n- 2 known vulnerability exists—could be a contributing factor.\n\n🔧 *Action Required:*\n- On-call engineers Marvin and Tal should roll back to the previous deploy version while isolating the Redis call regressions.\n- Re-run load tests locally with Maria's changes to confirm memory/caching issues.\n",
"execution_mode": "Automatic",
"conversation_starters": [
"What is the latest update on INC-123?",
"Generate an update for INC-123, we've found the root cause",
"Create a Slack update for incident INC-456",
"Summarize the current status of incident INC-789",
"What's the latest on the database outage incident?"
],
"tools": [
"^(list|search|track|describe)_.*",
"run_update_incident_with_ai_update"
]
},
"relations": {}
}MCP Enhanced CapabilitiesThe AI agent uses MCP (Model Context Protocol) enhanced capabilities to automatically discover important and relevant blueprint entities via its tools. The
^(list|search|track|describe)_.*pattern allows the agent to access and analyze related entities in your software catalog such as incidents, services, deployment etc., providing richer context for incident analysis. Additionally, we explicitly addrun_update_incident_with_ai_updateto the tools, which instructs the AI agent to call this specific action to update incident records with AI-generated summaries. -
Click
Createto save the agent.
Set up automations
We will create two automations to orchestrate the AI-enhanced incident management workflow:
- Trigger the AI agent when incidents are updated
- Send the update to Slack
Automation to trigger AI agent
-
Go to the automations page of your portal.
-
Click on
+ Automation. -
Copy and paste the following JSON schema:
Auto-generate incident update automation (Click to expand)
{
"identifier": "auto_generate_incident_update_on_update",
"title": "Auto-Generate Incident Update on Update",
"description": "Automatically generate incident update on update",
"trigger": {
"type": "automation",
"event": {
"type": "ENTITY_UPDATED",
"blueprintIdentifier": "pagerdutyIncident"
},
"condition": {
"type": "JQ",
"expressions": [
".diff.after.properties.status != .diff.before.properties.status or .diff.after.properties.urgency != .diff.before.properties.urgency or .diff.after.properties.priority != .diff.before.properties.priority"
],
"combinator": "or"
}
},
"invocationMethod": {
"type": "WEBHOOK",
"url": "https://api.getport.io/v1/agent/incident_update_ai/invoke",
"agent": false,
"synchronized": true,
"method": "POST",
"headers": {
"RUN_ID": "{{ .run.id }}",
"Content-Type": "application/json"
},
"body": {
"prompt": "Generate a Slack incident update for incident with target identifier {{ .event.context.entityIdentifier }}. The incident was updated with the following changes:\n\nPrevious Status: {{ .event.diff.before.properties.status }}\nNew Status: {{ .event.diff.after.properties.status }}\nPrevious Urgency: {{ .event.diff.before.properties.urgency }}\nNew Urgency: {{ .event.diff.after.properties.urgency }}\nPrevious Priority: {{ .event.diff.before.properties.priority }}\nNew Priority: {{ .event.diff.after.properties.priority }}\n\nIncident Details:\nTitle: {{ .event.diff.after.title }}\nDescription: {{ .event.diff.after.properties.description }}\nAffected Services: {{ .event.diff.after.relations.service }}\nOn-Call Engineer: {{ .event.diff.after.properties.assignees }}\nAssigned Team: {{ .event.diff.after.relations.assignedTeam }}\n\nRepository Metadata:\n- README Overview: {{ .event.diff.after.properties.readme }}\n- Last Push Date: {{ .event.diff.after.properties.repository_last_push }}\n- Last Contributor: {{ .event.diff.after.properties.repository_last_contributor }}\n- Known Vulnerabilities: {{ .event.diff.after.properties.repository_vulnerabilities }}\n\nIMPORTANT: This will be sent directly to Slack. You MUST format the response using Slack-compatible syntax:\n- Use *bold* for emphasis\n- Use emojis inline (🚨, 📋, 👥, etc.)\n- Use dashes - for bullet points\n- Use <https://url|label> for links\n- DO NOT use headers (###), raw markdown, or [label](url)\n- Add single line breaks between sections for readability\n\nYour incident update must adhere to the problem/impact/insight/action format",
"labels": {
"source": "Incident Update",
"entityIdentifier": "{{ .event.context.entityIdentifier }}",
"blueprintIdentifier": "{{ .event.context.blueprintIdentifier }}"
}
}
},
"publish": true
} -
Click
Createto save the automation.
Automation to send summary to Slack
-
Go back to the automations page of your portal.
-
Click on
+ Automation. -
Copy and paste the following JSON schema:
Send AI incident update to Slack automation (Click to expand)
{
"identifier": "send_ai_update_to_slack",
"title": "Send AI Incident Update to Slack",
"description": "Automation to post the response of the AI incident update to Slack",
"icon": "Slack",
"trigger": {
"type": "automation",
"event": {
"type": "ENTITY_UPDATED",
"blueprintIdentifier": "pagerdutyIncident"
},
"condition": {
"type": "JQ",
"expressions": [
".diff.after.properties.ai_update != .diff.before.properties.ai_update"
],
"combinator": "and"
}
},
"invocationMethod": {
"type": "WEBHOOK",
"url": "https://slack.com/api/chat.postMessage",
"agent": false,
"synchronized": true,
"method": "POST",
"headers": {
"RUN_ID": "{{ .run.id }}",
"Content-Type": "application/json; charset=utf-8",
"Authorization": "Bearer {{ .secrets.__SLACK_APP_BOT_TOKEN_<TEAM-ID> }}"
},
"body": {
"channel": "{{ .event.diff.after.properties.slack_channel }}",
"username": "Incident AI Assistant",
"text": "{{ .event.diff.after.properties.ai_update }}"
}
},
"publish": true
} -
Click
Createto save the automation.
You will need to add your Slack bot token as a secret in Port. Head to our guide on how to install the Slack app.
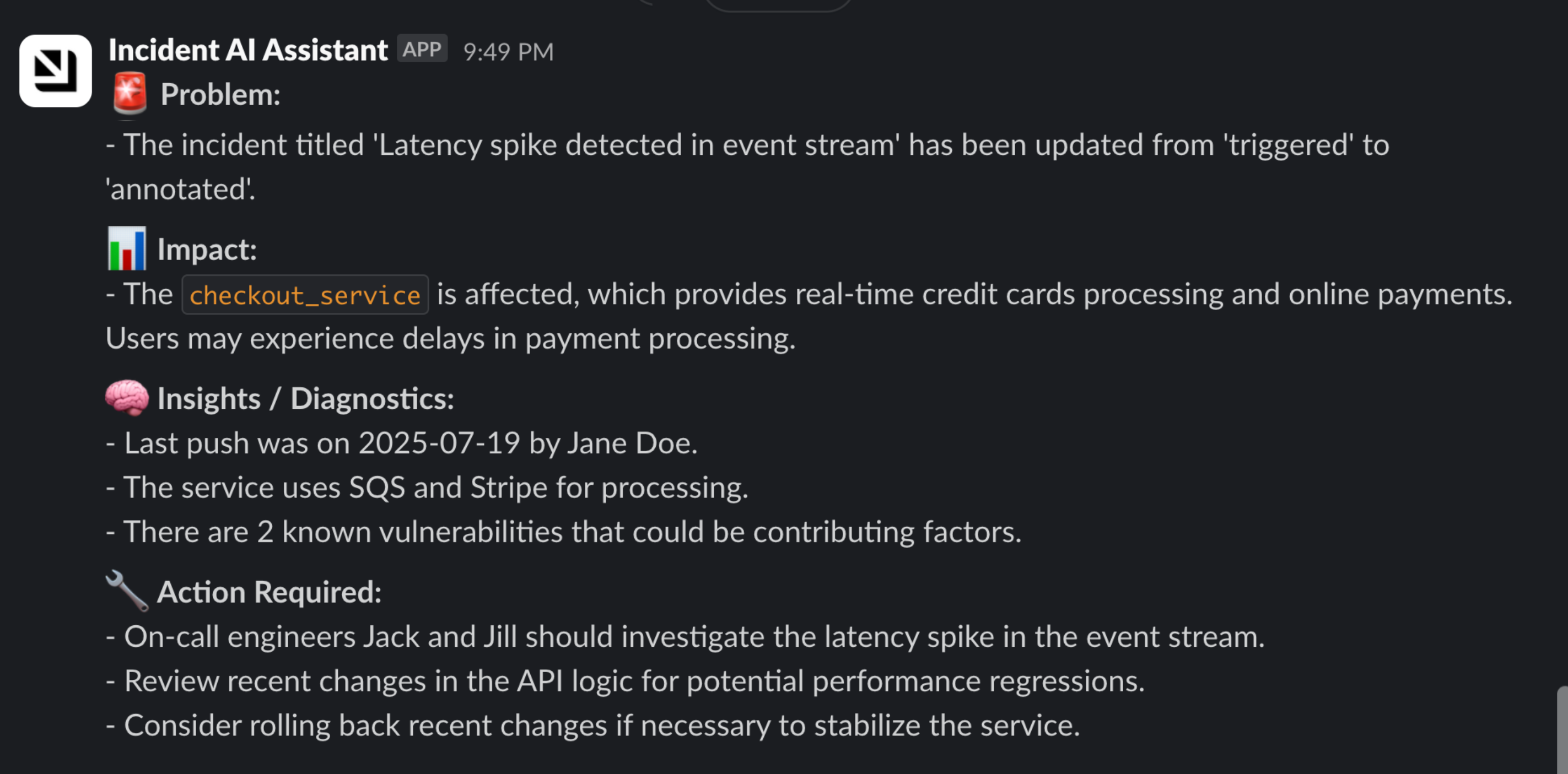
Below is an example notification sent to Slack:
Test the workflow
Now let us test the complete workflow to ensure everything works correctly.
Trigger a test incident update
- Go to the software catalog page of your portal.
- Find an existing PagerDuty incident or create a test incident.
- Update the incident's status, urgency, or priority to trigger the automation.
Verify the AI incident update generation
- Go to the AI Agents page of your portal.
- Click on the
Incident Update AIagent. - Check the
AI Invocationstab to see the generated incident update.
Check Slack notification
The AI-generated incident update should appear in your configured Slack channel with proper formatting and context.
Best practices
To get the most out of your AI-enhanced incident management workflow:
-
Monitor AI responses: Regularly review the quality and accuracy of AI-generated incident updates.
-
Refine the prompt: Adjust the AI agent prompt based on your team's specific needs and communication style.
-
Customize Slack channels: Configure different Slack channels for different teams or incident severities.
-
Add more context: Consider enriching incidents with additional metadata from other integrations.