Enforce AI coding security standards
Security engineers need to ensure that development teams follow proper AI coding security standards. This guide demonstrates how to use Port scorecards to automatically check if repositories have AI coding rules defined, helping enforce security best practices across your organization.
Common use cases
- Enforce security standards by ensuring repositories have detailed Cursor security rules and GitHub Copilot instructions
- Track security compliance across development teams with specific, actionable security requirements
- Identify security gaps in AI coding practices and prioritize remediation efforts
- Maintain consistent security standards across all repositories and development workflows
Prerequisites
This guide assumes the following:
- You have a Port account and have completed the onboarding process.
- GitHub integration is installed in your account.
While this guide uses GitHub, you can adapt it for other Git providers like GitLab, Azure DevOps, or Bitbucket by updating the file path mappings accordingly.
Set up data model
We will enhance the GitHub repository blueprint to include AI coding security rules and GitHub Copilot instructions, then configure the GitHub integration to ingest these files automatically.
Update the repository blueprint
To track AI coding security standards, we need to add properties for both Cursor security rules and GitHub Copilot instructions.
-
Go to the builder page of your portal.
-
Find and select your existing repository blueprint (e.g.,
githubRepository). -
Click on
{...} Edit JSON. -
Add the following properties to the
propertiessection:AI coding security rules properties (click to expand)
"cursor_authentication_rules": {
"type": "string",
"title": "Authentication Rules",
"format": "markdown",
"description": "Authentication and authorization security rules"
},
"cursor_command_injection_rules": {
"type": "string",
"title": "Command Injection Rules",
"format": "markdown",
"description": "Command injection protection rules"
},
"cursor_database_rules": {
"type": "string",
"title": "Database Security Rules",
"format": "markdown",
"description": "Database security and SQL injection prevention rules"
},
"cursor_file_upload_rules": {
"type": "string",
"title": "File Upload Security Rules",
"format": "markdown",
"description": "File upload validation and security rules"
},
"cursor_input_validation_rules": {
"type": "string",
"title": "Input Validation Rules",
"format": "markdown",
"description": "Input validation and XSS prevention rules"
},
"cursor_owasp_rules": {
"type": "string",
"title": "OWASP Top 10 Rules",
"format": "markdown",
"description": "OWASP Top 10 security vulnerability prevention rules"
},
"cursor_logging_rules": {
"type": "string",
"title": "Security Logging Rules",
"format": "markdown",
"description": "Security logging and error handling rules"
},
"copilot_documentation_instructions": {
"type": "string",
"title": "Documentation Instructions",
"format": "markdown",
"description": "GitHub Copilot documentation writing guidelines"
},
"copilot_general_coding_instructions": {
"type": "string",
"title": "General Coding Instructions",
"format": "markdown",
"description": "GitHub Copilot general coding standards"
},
"copilot_language_specific_instructions": {
"type": "string",
"title": "Language-Specific Instructions",
"format": "markdown",
"description": "GitHub Copilot language-specific coding standards"
} -
Click
Saveto update the blueprint.
This setup expects the following file structure in your repositories:
- Cursor rules:
.cursor/rules/security/*.mdfiles - GitHub Copilot instructions:
.github/instructions/*.instructions.mdfiles
Update GitHub integration mapping
Now we need to configure the GitHub integration to automatically ingest all the AI coding security rules and instructions files from repositories.
-
Go to the data sources page of your portal.
-
Find your GitHub integration and click on it.
-
Go to the
Mappingtab. -
Update the mapping configuration to include all the security and instruction properties:
GitHub integration mapping configuration (click to expand)
deleteDependentEntities: false
createMissingRelatedEntities: true
enableMergeEntity: true
resources:
- kind: repository
selector:
query: true
port:
entity:
mappings:
identifier: .full_name
title: .name
blueprint: '"service"'
properties:
readme: file://README.md
cursor_authentication_rules: file://.cursor/rules/security/authentication.md
cursor_command_injection_rules: file://.cursor/rules/security/command-injection.md
cursor_database_rules: file://.cursor/rules/security/database.md
cursor_file_upload_rules: file://.cursor/rules/security/file-upload.md
cursor_input_validation_rules: file://.cursor/rules/security/input-validation.md
cursor_owasp_rules: file://.cursor/rules/security/owasp-10.md
cursor_logging_rules: file://.cursor/rules/security/logging.md
copilot_documentation_instructions: file://.github/instructions/documentation.instructions.md
copilot_general_coding_instructions: file://.github/instructions/general-coding.instructions.md
copilot_language_specific_instructions: file://.github/instructions/language-specific.instructions.md
url: .html_url
defaultBranch: .default_branch -
Click
Saveto update the integration configuration.
The integration will look for files at the exact paths specified. Ensure your repositories follow the standardized file structure for consistent mapping across your organization.
Configure the scorecard
We will create a detailed scorecard that evaluates repositories based on their comprehensive AI coding security rules and GitHub Copilot instructions compliance:
-
Go to your builder page.
-
Search for the Service blueprint and select it.
-
Click on the
Scorecardstab. -
Click on
+ New Scorecardto create a new scorecard. -
Add this JSON configuration:
AI coding security scorecard configuration (click to expand)
{
"identifier": "ai_coding_security_standards",
"title": "AI Coding Security Standards",
"levels": [
{
"color": "red",
"title": "Critical",
"description": "Missing essential security rules - immediate attention required"
},
{
"color": "orange",
"title": "High Risk",
"description": "Missing critical security rules - high priority remediation needed"
},
{
"color": "yellow",
"title": "Medium Risk",
"description": "Some security rules present but gaps exist - moderate priority"
},
{
"color": "blue",
"title": "Compliant",
"description": "Most security rules implemented - good security posture"
},
{
"color": "green",
"title": "Elite",
"description": "Comprehensive security rules and best practices implemented"
}
],
"rules": [
{
"identifier": "auth_rules",
"title": "Authentication & Authorization Rules",
"level": "Elite",
"query": {
"combinator": "and",
"conditions": [
{
"operator": "isNotEmpty",
"property": "cursor_authentication_rules"
}
]
}
},
{
"identifier": "cmd_injection",
"title": "Command Injection Protection",
"level": "Elite",
"query": {
"combinator": "and",
"conditions": [
{
"operator": "isNotEmpty",
"property": "cursor_command_injection_rules"
}
]
}
},
{
"identifier": "db_security",
"title": "Database Security Rules",
"level": "Elite",
"query": {
"combinator": "and",
"conditions": [
{
"operator": "isNotEmpty",
"property": "cursor_database_rules"
}
]
}
},
{
"identifier": "file_upload",
"title": "File Upload Security",
"level": "Elite",
"query": {
"combinator": "and",
"conditions": [
{
"operator": "isNotEmpty",
"property": "cursor_file_upload_rules"
}
]
}
},
{
"identifier": "input_validation",
"title": "Input Validation & XSS Prevention",
"level": "Elite",
"query": {
"combinator": "and",
"conditions": [
{
"operator": "isNotEmpty",
"property": "cursor_input_validation_rules"
}
]
}
},
{
"identifier": "owasp_compliance",
"title": "OWASP Top 10 Compliance",
"level": "Elite",
"query": {
"combinator": "and",
"conditions": [
{
"operator": "isNotEmpty",
"property": "cursor_owasp_rules"
}
]
}
},
{
"identifier": "security_logging",
"title": "Security Logging & Error Handling",
"level": "Elite",
"query": {
"combinator": "and",
"conditions": [
{
"operator": "isNotEmpty",
"property": "cursor_logging_rules"
}
]
}
},
{
"identifier": "copilot_docs",
"title": "GitHub Copilot Documentation Standards",
"level": "Compliant",
"query": {
"combinator": "and",
"conditions": [
{
"operator": "isNotEmpty",
"property": "copilot_documentation_instructions"
}
]
}
},
{
"identifier": "copilot_coding",
"title": "GitHub Copilot Coding Standards",
"level": "Compliant",
"query": {
"combinator": "and",
"conditions": [
{
"operator": "isNotEmpty",
"property": "copilot_general_coding_instructions"
}
]
}
},
{
"identifier": "lang_standards",
"title": "Language-Specific Coding Standards",
"level": "Compliant",
"query": {
"combinator": "and",
"conditions": [
{
"operator": "isNotEmpty",
"property": "copilot_language_specific_instructions"
}
]
}
}
]
} -
Click
Saveto create the scorecard.
This scorecard evaluates repositories based on four key AI coding security standards:
- Security Instructions: Checks if repositories have AI-specific security guidelines
- GitHub Copilot Documentation Standards: Verifies presence of documentation instructions for AI tools
- GitHub Copilot Coding Standards: Ensures general coding instructions are defined for AI assistance
- Language-Specific Coding Standards: Validates that language-specific AI coding guidelines exist
You can modify these rules to match your organization's specific requirements by adjusting the property names, adding new conditions, or changing the scoring criteria.
Create dashboard
Now let's create a dashboard to visualize the AI coding security standards across your repositories, making it easy to track compliance and identify areas for improvement.
Set up the dashboard
- Go to your dashboards page in Port.
- Click on
+ New Dashboard. - Name your dashboard "AI Coding Security Standards".
- Add the following widgets to visualize your secure coding practices:
Add widgets
In the new dashboard, create the following widgets:
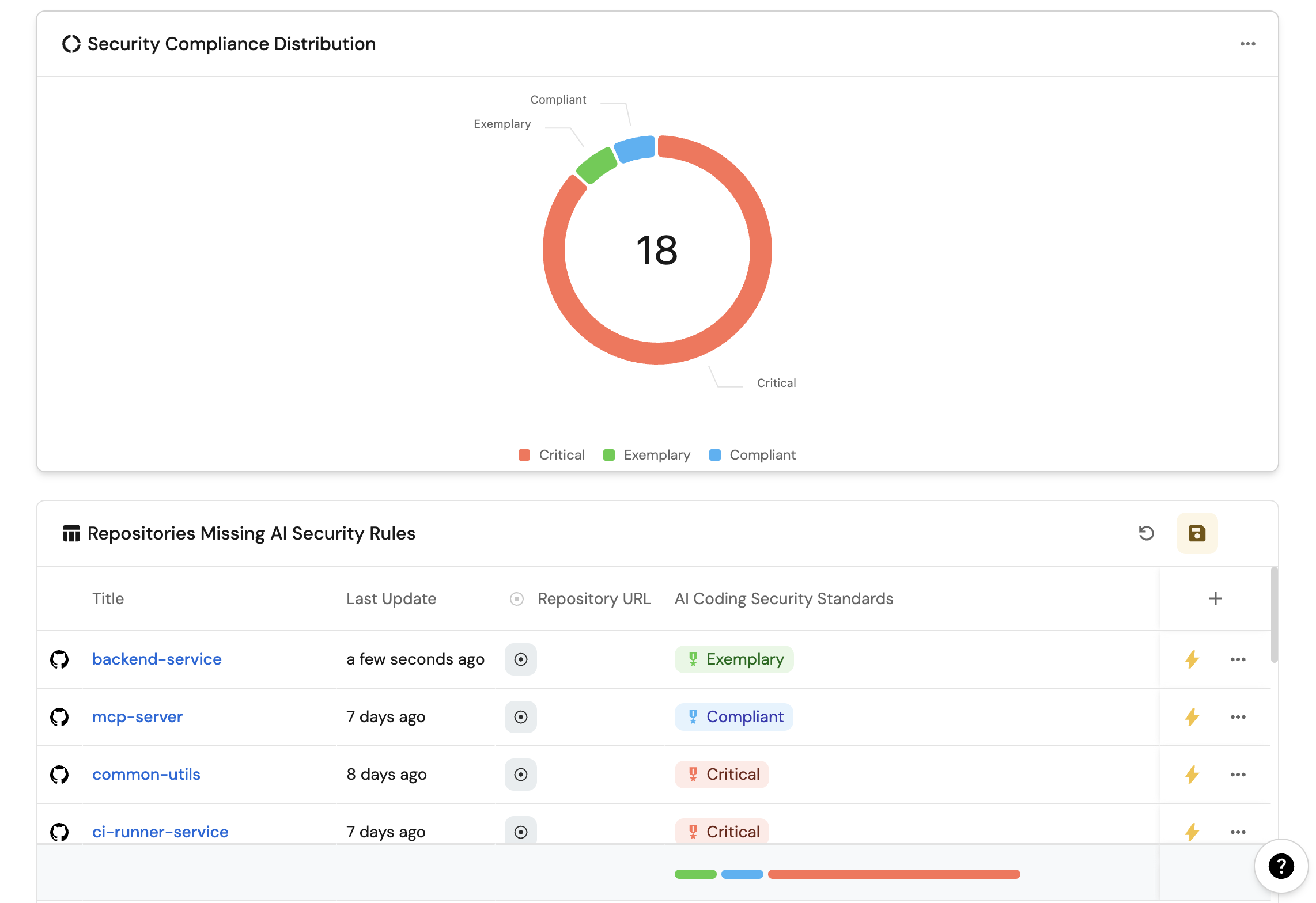
Overall security compliance distribution (click to expand)
- Click
+ Widgetand select Pie chart. - Title:
Security Compliance Distribution(add thePieicon). - Choose your repository blueprint (e.g.,
githubRepository). - Under
Breakdown by property, select AI Coding Security Standards. - Click Save.
Repositories without security rules (click to expand)
- Click
+ Widgetand select Table. - Title the widget Repositories Missing AI Security Rules.
- Choose your repository blueprint (e.g.,
githubRepository). - Add filter where
AI Coding Security StandardsequalsCritical. - Click Save to add the widget to the dashboard.
- Click on the
...button in the top right corner of the table and select Customize table. - In the top right corner of the table, click on
Manage Propertiesand add the following properties:- Repository Name: The name of the repository.
- URL: The link to the repository.
- Last Updated: When the repository was last updated.
- AI Coding Security Standards: The AI coding security rules content.
- Click on the save icon in the top right corner of the widget to save the customized table.